I had the opportunity to meet with Energy Secretary Jennifer Granholm for about 5 minutes this past week on her visit to Idaho National Laboratory.
In my short time with her, I found Secretary Granholm energetic and inquisitive.
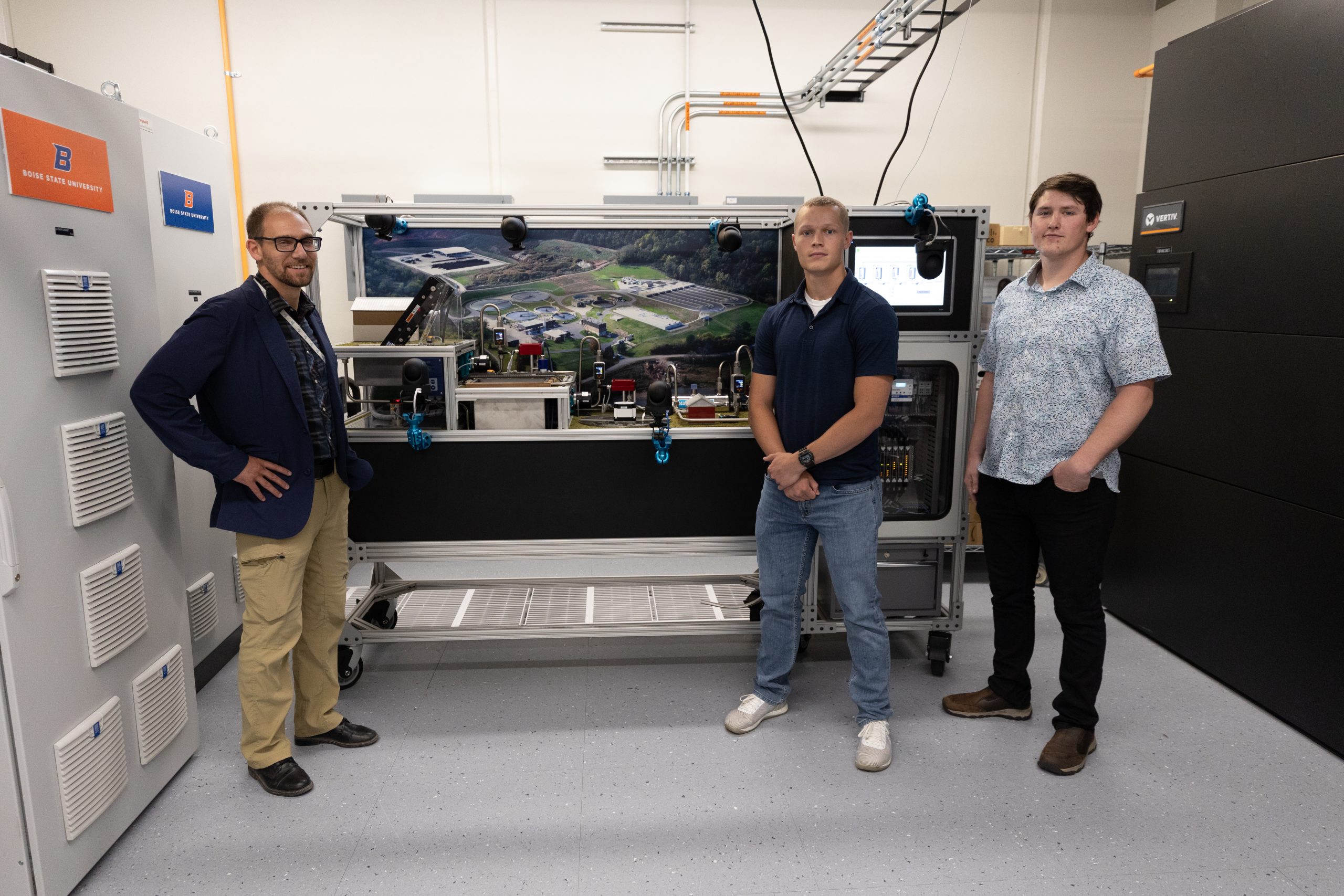
INL’s Eleanor Taylor, two ISU students interning at the INL, and I, led Secretary Ganholm and Idaho Representative Mike Simpson on a tour of the Cybercore Integration Center University Laboratory (CICUL).
As an INL/ISU joint appointee, I have the opportunity to leverage INL’s two decades of leadership in industrial cybersecurity to help create the next generation of engineers, technicians, analysts, managers, and researchers to defend the country’s critical infrastructures — it is an exciting mission!
We intend to use the CICUL to design, pilot and accelerate adoption of cyber-informed engineering of industrial control systems (ICS) by developing transformative educational experiences and conducting innovative research.
So, there was no better way to show our mission and our progress than by turning the time over to a pair of fantastic students/interns to describe the equipment in the laboratory, and explain their summer projects.
They did a great job describing the wastewater treatment skid, the user manual and startup guide they created, and their plans for allowing universities to integrate the skid into their educational offerings. Great opportunity for them!