The Secretary and CICUL
I had the opportunity to meet with Energy Secretary Jennifer Granholm for about 5 minutes this past week on her visit to Idaho National Laboratory.
In my short time with her, I found Secretary Granholm energetic and inquisitive.
INL’s Eleanor Taylor, two ISU students interning at the INL, and I, led Secretary Ganholm and Idaho Representative Mike Simpson on a tour of the Cybercore Integration Center University Laboratory (CICUL).
As an INL/ISU joint appointee, I have the opportunity to leverage INL’s two decades of leadership in industrial cybersecurity to help create the next generation of engineers, technicians, analysts, managers, and researchers to defend the country’s critical infrastructures — it is an exciting mission!
We intend to use the CICUL to design, pilot and accelerate adoption of cyber-informed engineering of industrial control systems (ICS) by developing transformative educational experiences and conducting innovative research.
So, there was no better way to show our mission and our progress than by turning the time over to a pair of fantastic students/interns to describe the equipment in the laboratory, and explain their summer projects.


They did a great job describing the wastewater treatment skid, the user manual and startup guide they created, and their plans for allowing universities to integrate the skid into their educational offerings. Great opportunity for them!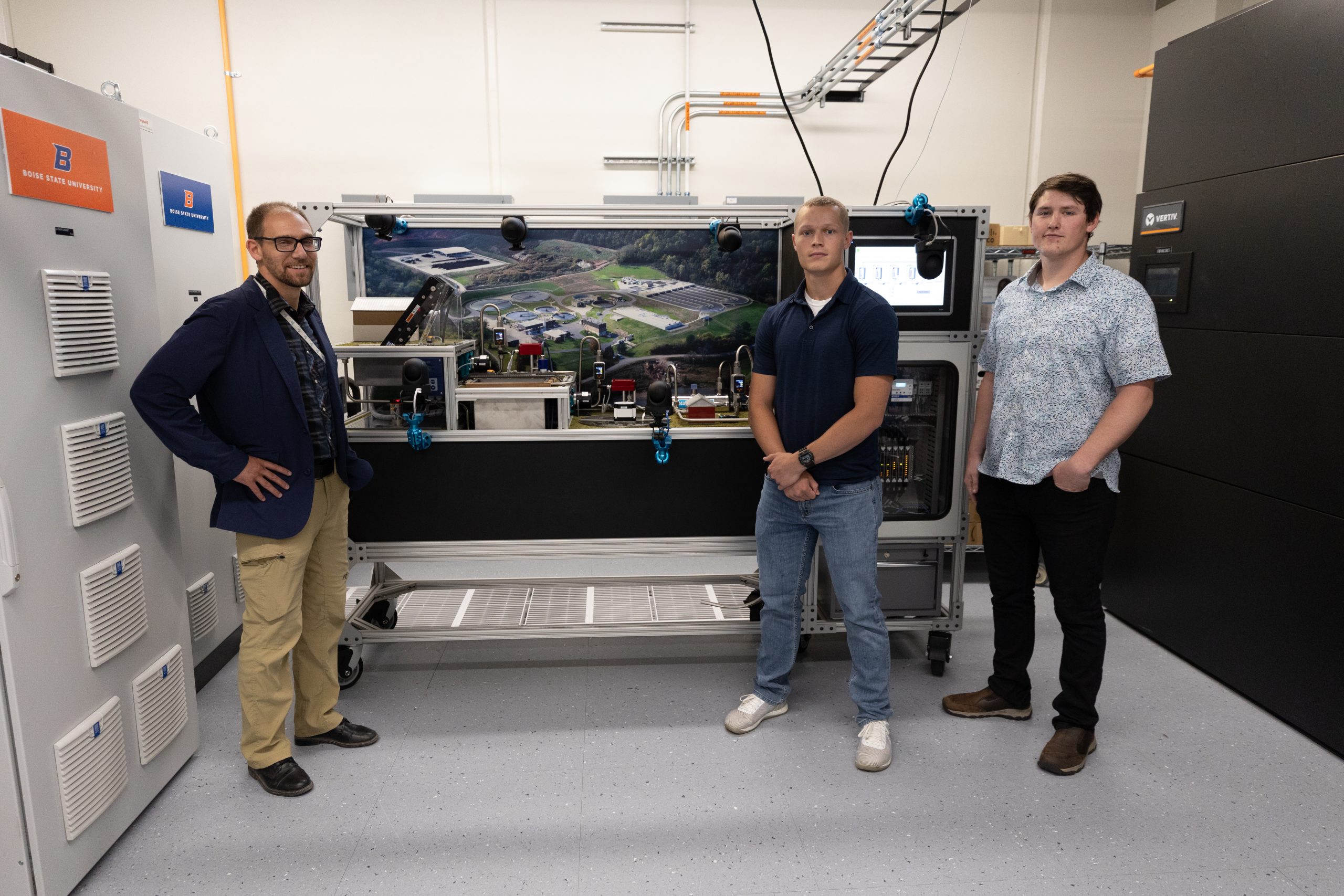


ISU-INL publication cited in support of proposed legislation
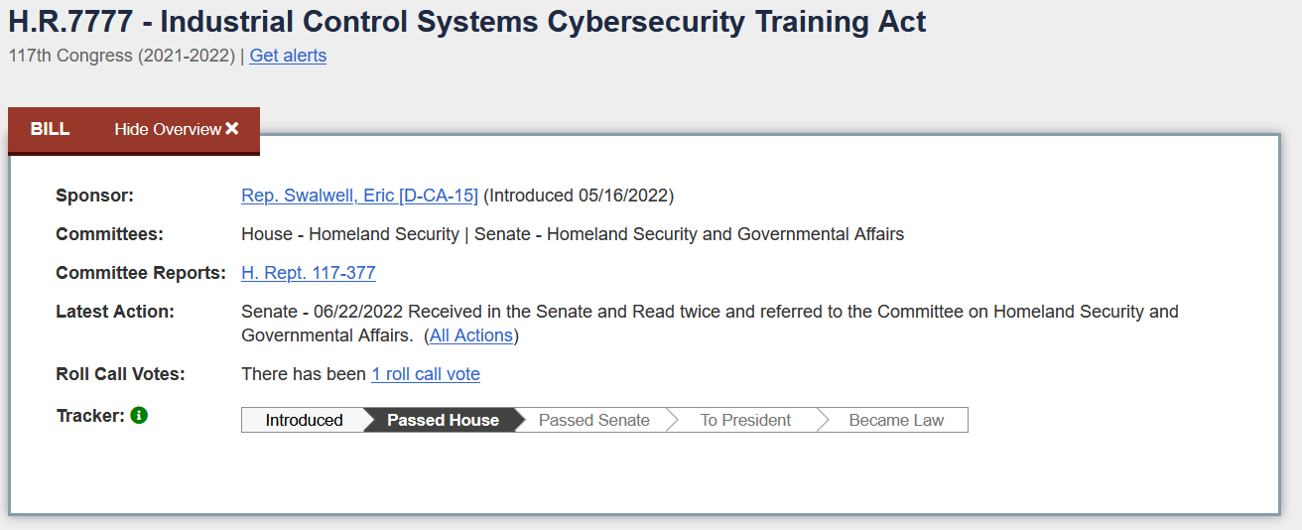
I had a neat professional experience the other day. Research I conducted in collaboration with the INL was cited as a justification for proposed legislation: HR 7777 The Industrial Control Systems Cybersecurity Training Act.


Here’s the key quote from the House Committee Report:
Because those working in ICS cybersecurity must understand how technology impacts industrial operations, there are additional types of training required. According to a group of industrial cybersecurity experts convened by Idaho National Laboratory and Idaho State University, there are six industrial cybersecurity knowledge domains that are not included in traditional cybersecurity education: industrial operations, instrumentation and control, equipment, communications, safety, and regulation. Expanded Federal support for ICS cybersecurity training would ensure more workers have the necessary, specialized skills to protect ICS.
The report is citing the “Building an Industrial Cybersecurity Workforce: A Managers’ Guide“, published jointly by INL and ISU. I blogged about the document in December 2020. It is also embedded as an appendix to my doctoral thesis.
The bill, which essentially instructs the CISA to offer virtual and in-person training at no cost to participants, passed the House on June 22.
While I note that free ICS security training has been part of DHS, ICS-CERT and CISA’s offerings for nearly 20 years now, I am excited to see the idea that industrial cybersecurity is different gaining traction at a national level!
Five year curriculum review
We have been operating the country’s only two-year hands-on industrial cybersecurity degree program for six years! That’s hard to believe.



We have produced some great graduates and placed them with great employers, including the INL, Accenture, West Yost, Automated Dairy, and Simplot.
In order to ensure the relevance of the program, we recently conducted a comprehensive curriculum review with the ESTEC Executive Director and seven faculty members who teach program courses.
We walked-down every course in the program, including title, description, learning objectives, syllabus, mapping to program objectives, assessments administered, and educational materials (including laboratory equipment) used.
The review was a big deal and made for some long sessions. We asked hard questions and had meaningful discussions about what to include or exclude. For example:
- We decided to add a new course to provide deeper coverage into operating systems. This meant we were going to have to cut a course. Where instructors are limited, and some courses are taken by students in multiple programs of study, this was a tough decision to make.
- We debated whether we were spending too much time on units of measure, including conversions of temperature, pressure, level and flow. At first the repeated emphasis on this topic seemed unnecessary; but, frank discussion bore out that if a student cannot do this, they will be ineffective at understanding/describing both the causes and consequences of an incident. We decided that assignments dealing with this topic needed to include context that reinforced their relevance to industrial cybersecurity.
- We determined to re-emphasize the importance of reading and creating engineering diagrams, especially piping and instrumentation diagrams.
What you might not realize if you are unfamiliar with formalized education administration is that some curriculum changes require approval of the entire university curriculum council — meaning that changes will not appear in the catalog for a year or more!
In all, I felt like this detailed review represented a new level of maturity for ISU’s industrial cybersecurity program. I am excited for how these changes will better prepare our students to tackle the complexity of an exciting and evolving field.
17 Graduates
This was a great school year.
We had 17 students in the Industrial Cybersecurity program cohort last August. All 17 graduated this Spring — either with their first Associate Degree (2 year program), or with an Intermediate Technical Certificate (1 year program on top of a previous degree).



I love the cohort model be because it allows students to work with people who have different backgrounds. Four cohort members were veterans. Two had previous master degrees. One was a graduate of the Naval Academy. Several were over 40. A couple were barely 20. Many of the students had lined up jobs and internships before graduating.
As the program has grown, the curriculum and delivery have improved. On the whole, I’d say that this cohort made it farther than any previous group. As we completed a Jeopardy-style review for the program-comprehensive knowledge exam, I loved it when students pointed out errors with the questions!
I am excited to see where these students go and how they influence not just their employers, but the industry and the world!
IT-OT Fundamentals Course
We launched a new course: ESET 181 IT-OT Fundamentals about three years ago. I am the primary course author. I haven’t done a lot of looking, but it could be the only such course in the country.
Industrial Cybersecurity students take the course in their first semester. It is also a required course for ISU’s Electrical Engineering Technology (EET) students. This means that we teach two sections each fall, and one section each spring (EET has a start in the spring and fall).
The first time I offered the course, it was rough. Industrial Cybersecurity students really liked it. But EET students couldn’t see why they needed to learn about computers and networks.
So, we sat down and really worked through the course to make it relevant from day 1. We structured the hands-on elements of the course around a semester long project-based learning (PBL) experience.
I love PBL — especially when the projects are applicable to real life. Because we are in Idaho, we based the project around upgrading the automation system for dehyrated potatoes.
Students read a real news article and a real job posting explaining the needs of a local employer.
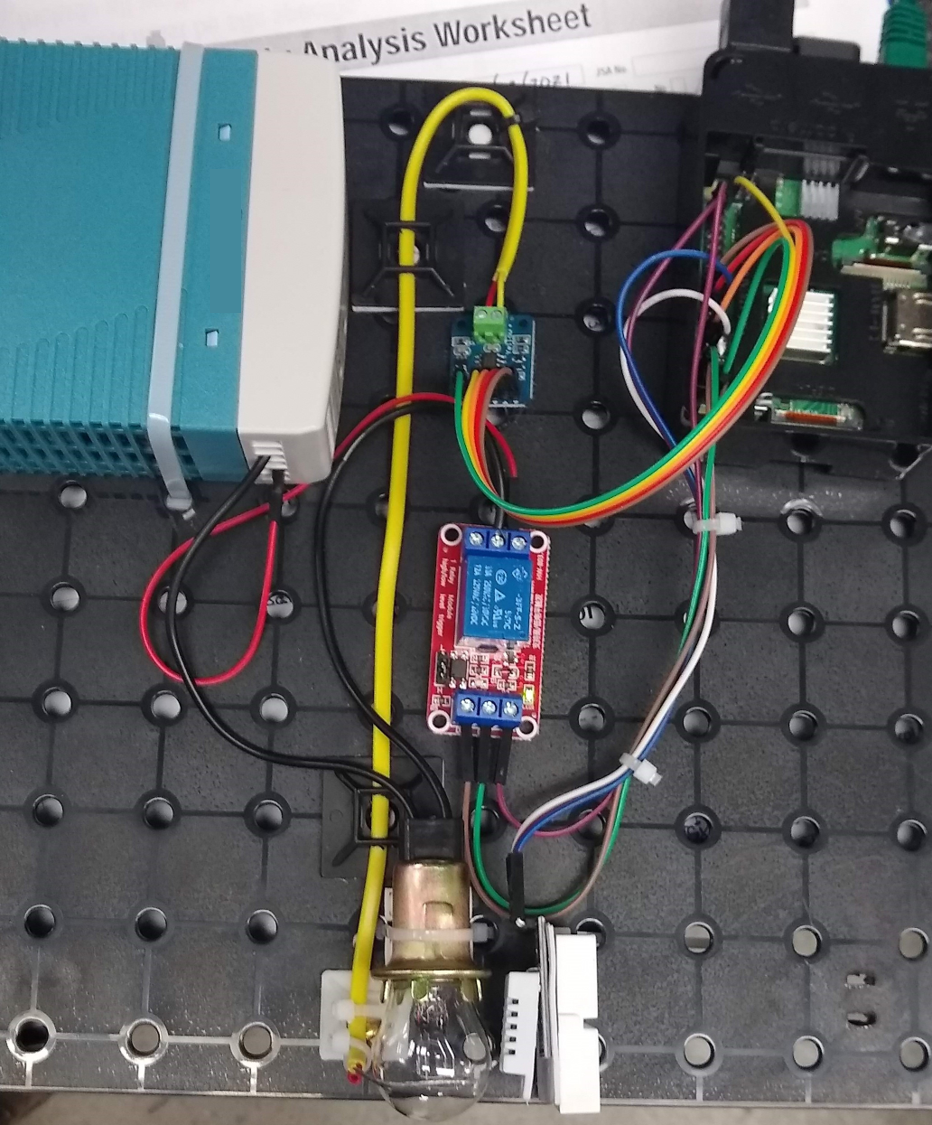
The students then learn about the convergence of IT and OT with a variety of hands-on experiences. These include tearing down a computer, designing a SCADA HMI screen, creating a simple temperature control loop with a Raspberry Pi, performing basic switch configuration, and many others. In the end, these aggregate into a final project.
The image below shows the kit students build as they learn about the concepts. Temperature control loop consists of a light bulb, thermocouple, and relay board.


We’ve made several enhancements over the years (and have more to make!), and I am pleased to say we are hitting the mark. Here is some feedback from three of our EET students who just completed the course:
The most important thing I learned from the project was how interconnected OT and networking are. When drawing the network diagram I realized how the two are becoming closer and closer together. I learned that even though I am in an OT role, a good understanding of IT will put me leaps ahead…
The most important thing I learned form the project was the importance of a network and why the Purdue model is such a useful tool. When everything is connected and running it has to work in sync or the whole system doesn’t work. The networking is so much more than I thought it was and I do have a more profound respect for it.
The project helped me understand aspects of IT/OT the most. These were the networking of OT devices, setting up networks, and I was so grateful for the many examples of real world situations and scenarios. I can definitely see myself reflecting on this class and the learning activities as I enter and progress through my career.
I wish this program had been around when I was a student
Last year we placed a graduate with a water and wastewater systems engineering firm — that does SCADA master plans, HMI design, and PLC programming, along with cybersecurity and resilience consulting.
The graduate has had several of this colleagues and supervisors come to tour of our instructional facilities, and discuss our curriculum.
On a recent tour, we stopped at looked at the conduit bending station I blogged about several weeks ago.



We looked at our flow control trainers and talked about the custom multiplexing printed circuit board.
We stopped to examine the “pressure wall” in our mechanical engineering technology area. Here our students can adjust the height of pumps that move liquid through pipes of various materials — copper, PVC, steel. They can open and close valves by hand. And they can hook the pipes to pressure transmitters. They get to calculate pressure head and think about turbulent flow.
The graduate said “I’ve heard so many people say ‘In my job, don’t use anything I learned in school’; but, I feel like I use everything I learned in this program.”
I smiled.
Some may ask what these things have to do with cyber security — well, these determine the effects of an attack. This is what you can do if you control the pumps and the valves.
Our guest was impressed: “I wish this program had been around when I was a student!
I said “Me too. That’s what we set out to build!”
Just one “B”
One of the things I enjoy most about being an instructor is getting to know my students. Our program has a capacity of 20 students, and runs as a cohort. Because I teach several classes at a time (this semester I am teaching five), I get to spend quite a bit of time with the students.



I love getting to know my students as individuals. I love finding out where they came from, and what interested them in cybersecurity. I come to appreciate their unique experiences and points of view. I enjoy their creative abilities. I especially like giving them individualized feedback.
Near the conclusion of each school year, The University alumni organization puts on an awards ceremony for 11 outstanding students — one or two from each college at the University. This year I nominated a student to receive our Outstanding Student Achievement Award — and I was pleased that he was chosen to receive that honor.
This student — who happened to be from Pocatello (our university town) — did something unique and impressive: He asked one of his teachers from grade school, one from middle school, and one from high school to be present at the ceremony; then, during his acceptance remarks, he shared a short experience where each teacher had positively influenced his life.
I am sure it was a rewarding moment for those teachers to feel that they had influenced this student in some small way.
According to information shared openly about his academic performance, this student had a 3.98 (scale of 4.0) GPA: he had received one single B during his entire undergraduate studies.
Now, before the ceremony began, I was chatting with another instructor from my department. He said to me “I am very happy for this student. But when I realized that I had given him his only B, I felt like I might have ruined his perfect run.”
I responded in jest “Well, he will remember you one way or another!”
Then, I smiled immensely when in his acceptance speech, after honoring his grade school, middle school, and high school teachers, the student called my colleague’s name and said “he is a demanding teacher who expects his students to work hard, knowing it will serve them well as professionals, and I am thankful for the learning experience I had in his class.”
That was outstanding.
IT-OT Current Events Assignment
I ask students in our IT-OT Fundamentals course to create a short slide presentation about a current event in industrial automation — which they then share with the class.
The assignment increases their familiarity with industry trade publications and gives them a sampling of intriguing news.
Ethernet to the transmitter (SPE), and connected pumps were a couple of developments that caught my attention — because they represent a transformation of both input and output. Couple this with cloud services, and things can get very interesting.



A couple of weeks ago I made a trip to Utah State University in Logan, where we talked with the fine people running the innovative Center for Anticipatory Intelligence. At lunch, one faculty member asked me a very thoughtful question (especially for someone who isn’t a cybersecurity person): “Do you think the new systems being built today are more or less vulnerable than what we’ve created in the past?”
My response? “On the whole, I am afraid we are making the most vulnerable industrial processes we’ve ever had.”
That should give us a lot to think about – with important implications for how we educate and train the emerging workforce.
Bending Conduit?
Here is something you might not have expected: We have all our cybersecurity students take an energy systems hands-on lab where they spend a session learning to bend metal conduit. We actually have a nice little conduit bending station. Students get to try making several different bends. It is not necessarily an easy thing to do!



Cybersecurity students have some times wondered — especially in the heat of the moment — “Why am I learning to bend metal conduit? This is not what I ever intend to do as a professional!”
I tell them, “I don’t think you will ever bend conduit. But you will never look at a facility — and especially the conduit — the way same again. That’s what makes us different from ‘traditional’ cybersecurity programs.”
To me, a fundamental part of bridging the IT-OT gap is appreciating another perspective — learning to value the training, competencies and objectives of someone else; and, maybe even to revere differently competent technical professionals as artists in their own right!
The conduit bending exercise also gets the students thinking about the cables — not just power, but communications. Near the end of the program, in our Critical Infrastructure Defense class, we discuss attack vectors — who, when, and where could a structured threat actor strike? The point of the cables comes back up — and when re-enforced with examples of tapping tools — the security implications of every inch of cable suddenly make a lot more sense!
Interview night
A couple of years ago we had planned to carry out an Industrial Operations Combine for all students in ESTEC programs. We intended to pattern the Combine after the NFL combine, where regional industrial employers could come and watch students perform a variety of simple tasks, and conduct interviews.
Unfortunately, COVID-19 forced us to re-think our approach. Instead, for the past two years, we have held an “interview night” for industrial cybersecurity students.


The purposes of this event are to:
1. Allow program stakeholders to interact with the potential employees produced by the program.
2. Give every student a short and realistic interaction with a potential employer (regardless of whether the interviewer is actually hiring at the moment).
Interview Night format:
* Interviews conducted via Zoom.
* Each interview lasts ~30 minutes.
* Each interviewer conducts two interviews.
* Interviewer and student are paired in a Zoom breakout room.
Interviewers are free to craft their own interview questions, but they could include:
* What interests you most about a career in industrial cybersecurity?
* What course or project was engaging to you?
* We often face INSERT RELEVANT CHALLENGE, how would you suggest we address that?
We have 17 students finishing up the industrial cybersecurity portion of the program — be it AAS, or Intermediate Technical Certificate. About 7 of those will continue on for a Bachelor degree, and enter the workforce in January or May 2023, which leaves 10 that would like to enter the workforce in May. We have four or five students who will graduate with their BAS this May (2022).
Of these 17, twelve were able to attend Interview Night. We had 14 industry representatives show up — meaning that every student got two half-hour interviews! Industry reps hailed from INL, West Yost, Accenture, Nucor, 1898, TSA, Mandiant, Siemens, Duke Energy, and QED. I am so thankful for their fantastic support.
I would say that this year’s interview night was one of my favorite parts of my five-year adventure in education — the opportunity to show off the product– the students — to the consumer — industry representatives!