The courses
I am sure I will address this in greater detail in the future, but I wanted to tell readers about the actual courses in the Industrial Cybersecurity Engineering Technology program at Idaho State University.
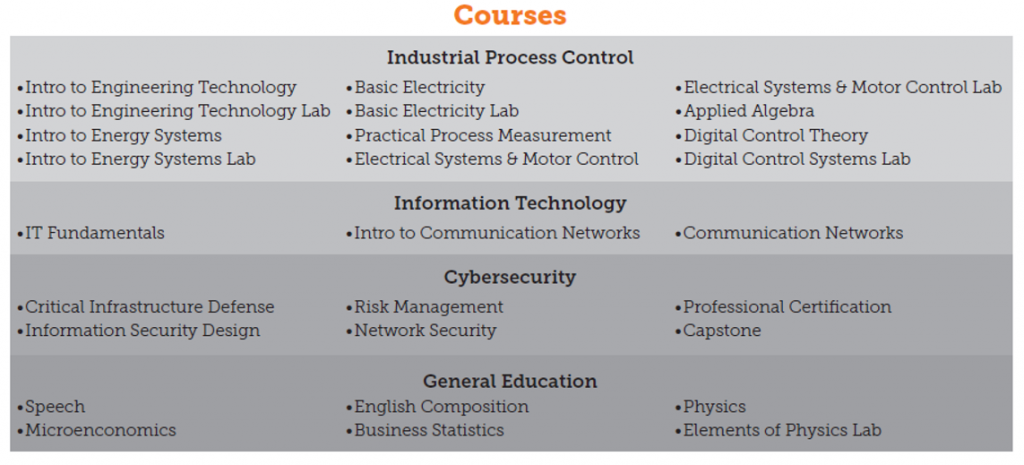
You can see from the list that 13 of the 28 courses fall into the industrial process control category, six fall into cybersecurity, and three fit under IT. This is a specific and intentional program design intended to make sure our graduates are ready to enter the industrial/plant floor environment.
In fact, what we really want is students to graduate from any of the other hands-on engineering technology AAS degrees offered in our department: electrical, instrumentation, mechanical, nuclear operations, then go get a job and work for a couple of years. With real-world experience under your belt, return to enroll in Industrial Cybersecurity, where they can bring valuable real-world perspective into the classroom, and increase their earnings potential.
Tips for employers interviewing industrial cybersecurity candidates
As we come down to the end of the semester here, my students are interviewing for internships and jobs.
Based on student feedback, sometimes it seems that employers may not be attuned to the skill sets they need or know how to identify individuals who have the right competencies.
To aid employers in evaluating our students we encourage our students to maintain a portfolio of their projects, including photographs and final presentations from various courses, which they invite employers to review.
In addition to reviewing the portfolio and asking some questions about it, I’ve created the following short list of sample questions that help employers discern between an IT security person and an industrial cyber person capable of bridging the IT-OT divide:
- Can you share your experience programming PLCs?
- Will you tell me about how you protect technician lap tops?
- How do you differentiate between a physical failure and a cyber attack?
- What steps are involved in calibrating a temperature transmitter?
- How does one segment an industrial network?
- What challenges have you faced when creating an ICS asset inventory for security purposes?
Security-related questions for facility tours
A previous post described that our industrial cybersecurity students take at least five tours in their first year.



I created a list of questions that industrial cybersecurity students might ask their tour guide. We look specifically at: Asset inventory, network issues, change detection, external connections, recovery, security, IT-OT gap.
Here’s a sampling:
- How many different PLC vendors do you have?
- Has a process ever shut down as the result of a network issue?
- What procedure is used to make a control logic change (PLC programming)?
The key idea is encourage application of in-class principles to the real world.
It is interesting to hear tour guide responses.
I’ve attached the entire question set in the curricular materials section of the Web site. Happy touring!
Sandworm Discussion Results
A couple of weeks ago I mentioned that Andy Greenberg’s Sandworm is required reading in my Critical Infrastructure Defense course, and I posted a study guide for others to use.



We are maintaining the same schedule of chapters each week, but I provided students the following guidance:
- Pose one thoughtful question about the assigned chapters by Wednesday
- When posting, please put the main idea or topic of your question as the Subject line. This allows potential respondents to sift through the topics without having to open each post. Moreover, forcing yourself to write a concise, meaningful subject is an important written communication skill.
- I consider the ideal format for the initial question post to include the following:
- Brief background
- Cite the chapter (maybe even page number) — to allow other participants to know exactly what you are referring to.
- Make an observation
- Ask a question that elicits thoughtful responses
- Questions can address something you want to understand better OR something you find interesting to discuss. The following question formats may be useful
- What was meant by…?
- Can you help me understand…?
- What is the difference between…?
- How would this apply to …?
- Does anyone else…?
- What does the class think about …?
- Thoughtfully respond to two classmate’s questions by Sunday
- Please re-respond to those who answer the question you posed
We’ve had some fantastic questions and ensuing discussion. For example, here are two questions posed by students (which they allowed me to share publicly):
In Chapter 29, it discusses how there are still different debates about NotPetya’s intentions. What debate do you think is the most cogent for NotPetya’s intentions?
We can see here that the student picked out the concept of intent, and noted that this is a challenging topic. A question like this can lead to discussions about threat intelligence, attribution, attack design, and evaluation of competing hypotheses, among other possibilities.
Here’s another:
For these chapters about NotPetya and how it spread I kept thinking about the Systems of System Analysis and how even outside ICS environments it would be beneficial to all organizations to go through this approach with their networked systems and software as a service system’s. For example, the book talked about hospital dictation software and how it was affected by NotPetya. I am assuming they never considered that as a crucial part of their day to day operations. What are your thoughts on applying system of system analysis on more than just ICS but potentially the enterprise side of the organization? Do you think this would have been beneficial to the hospitals or other organizations affected by NotPetya?
In this case the student took a core concept we cover in the class (system of systems analysis) and found where it would have applied within the Sandworm narrative. Then, the student realized the concept probably doesn’t only apply to industrial environments. This can lead to a discussion about biases of human cognition, differences in expertise necessary to conduct SOSA in an ICS vs IT environment, critical vs non-critical dependencies, and so on.
What I love about using an applied text like Sandworm is that it comes with the context for application — engaging the imagination. Standard texts may encourage vocabulary acquisition, but don’t get to this level of richness.
COVID-19 means no more facility tours this school year
One of my favorite parts of the Industrial Cybersecurity program are the tours our students get to take. We try to get them 5 field trips in the first year alone. This generally includes the ISU heat plant, Great Western Malting, the Simplot Don Plant, Amy’s Kitchen, and a nearby substation. We even bring our own headsets so all students can hear the guide.



Here’s a photo of our industrial cybersecurity students at Amy’s Kitchen. One of our instructors is explaining a principle of operation pointing to an instrument panel. It is super cool that an ESTEC Instrumentation graduate who works at the facility was our tour guide!
For the first couple of tours students are a bit lost, but as the semester progresses, they gain vocabulary and use industrial equipment in educational labs. By the final tours they are excited as they understand how things are working. They can converse with the guide and ask meaningful questions.
So, it was a bit of downer that COVID-19 cut the tours short for the year. We will do our best to get these students into more facilities next fall!
Sandworm Book Review
I while ago I finished Andy Greenberg’s Sandworm. Here’s my single-sentence review:
Couched within the fascinating journeys of real-world characters striving to understand the implications of our evolving cyber world, no other book provides as rich and accessible a discussion of cybersecurity, threat intelligence, critical infrastructure, and nation-state threat actors as Greenberg’s Sandworm.



I’ve read many of Greenberg’s articles over the years. I admire his breadth of coverage, and ability to take complex topics and prepare them for a popular – though tech literate – audience.
I appreciated that the book represents Greenberg’s personal journey to answer the question “who is Sandworm?”, making an easy journey for the reader as well. While I found myself laughing – and even shouting out loud – in agreement, I also frowned a time or two. As someone who spent a decade of his life dedicated to understanding and explaining the cyber threat to critical infrastructure, things that seemed obvious to me were sometimes revelations to Greenberg; and, several conclusions I thought were plain wrong. But knowing that he was simply (and eloquently) describing his journey encouraged my patience.
Greenberg seems naturally a people person – which contributes to the book’s accessibility. I was surprised and pleased by his effort to paint the personalities of the main cast of characters.
John Hultquist and I worked together on Sandworm-related threat intelligence at iSIGHT Partners (which acquired my firm Critical Intelligence in March 2015) and later FireEye. I ran the Attack team, and Hultquist ran the Espionage team. We offered complimentary coverage as I analyzed the industrial control aspects of Sandworm activities. When the electric transmission pylons serving Crimea were blown up in fall 2015, we collaborated to warn our customers that cyber attack against Ukraine utilities would be a likely Russian response. We presented together on the S4 Main Stage on the first Ukraine outage just weeks after it occurred. In Sandworm, I was pleased to see Hultquist’s own fascinating story presented to the world.
Rob Lee and I crossed paths many times over the course of his rise. I found Andy’s description of Rob excruciatingly accurate. Rob’s intelligence, contagious passion and persuasive ability has driven him to stardom, and attracted great talent into his firm, Dragos. Early on he invited me to join him, too. But I had an alternate vision of my future.
In all, I decided to make this book mandatory reading for students in my Critical Infrastructure Defense course. Students remember stories – and Sandworm provides rich context for exploration and application. Plus, I have developed my own profound perspectives around these same events.
I created a Sandworm Discussion Guide, which you can find in the Curricular Materials section of my Web site at this link. Happy teaching!
Teaching to the test? continued
This post is part 2 of “teaching to the test“.
We just reviewed differing opinions on whether it’s okay to teach to the test, and I promised to tell what approach I was taking in ISU’s Industrial Cybersecurity Program.



In my program, I require a Professional Certification course. It’s really a professional preparation course, but the main thrust is obtaining the SSCP cert.
Why?
- First, I want my program to tie to some external validation point.
- Second, I want students to enter my program clearly expecting to take and pass the exam.
- Third, no single existing certification will accurately reflect what my students know and can do as they bridge IT and OT.
- Fourth, the class covers a breadth of cybersecurity content not covered in other classes – so it’s not just review.
I specifically chose to have a class that teaches to this exam because that way the “narrowing of scope” that concerns Ravitch and Schou (see previous post) are concerned is confined to a single space and time.
If content from that course spills into other courses, or vice versa, that’s a benefit rather than a drawback.
I chose the SSCP cert because it is an appropriate medium level certification. It has a reasonable price point for students, and is tied to a nonprofit membership association — the (ISC)2. Thus, the certification is tied to professionalism rather than merely a credential. Moreover, maintenance of the certification requires continuing professional education credits. It also requires adherence to a formalized statement of ethics. I encourage my students to participate in the ISC2 Idaho Chapter.
Students are required to take the exam, and it’s costs are included in the course fees.
I also use this course to ensure students transition to the workplace. They are sharpening the resumes, honing their social media profiles, and conducting mock interviews.
Teaching to the test?



Courtesy Allison Wood CC 3.0
Industrial Operations Combine



The club determined to organize an Industrial Operations Combine – modeled after the NFL Scouting combine. We invite potential employers to come and see the students in action completing a challenge such as wiring up a PLC, interpreting a P&ID, running Wireshark. This gives them a great feel for what our students can really do, rather than just what a resume says.
Participating employers receive resumes and contact details for all candidates, and can schedule interviews for the next day. If this sounds intriguing, come and check it out. Then sign up to bring a challenge next year!
Scipio Africanus
For about two years, I shared an office on 17th street in Idaho Falls with Michael J. Assante. During that time, he recommended I read “Scipio Africanus: Greater than Napoleon” by noted military historian B.H. Liddell Hart.
As I contemplated Assante’s legacy, I recalled the recommendation, and decided to take him up on it!



In the book, Hart describes the life and military career of Scipio Africanus. At about age 25, the Senate sent Scipio to Spain against the Carthaginians, where, together with their allies, they had slain Scipio’s father and uncle, who were also Roman military leaders.
Hart describes Scipio’s brilliant battlefield strategy and tactics, including logistics, surprise, rhetoric, self-control, and interpersonal skills. Ultimately, Scipio leads the Romans on to conquer their rivals, the Carthaginians, who were led by the revered Hannibal.
Hart makes the case that Scipio Africanus is likely the greatest general of all time. He underscores his claim by pointing out that Napoleon, another contender for the title “greatest”, was ruthless in the pursuit of personal advantage, unnecessarily destroying many of his own countrymen, while Scipio worked tirelessly to preserve his. Hart credits Scipio with laying the foundation of the Roman empire as the crib of Western Civilization.
One of my favorite parts of the book was the story of an elderly Scipio asking an elderly Hannibal who was the greatest military captain of all time. Hannibal lists three notable captains — among whom Scipio is not named. Taking an alternate approach, Scipio asks Hannibal: had you beaten me in Africa then who would it be? “Of course,” said Hannibal, “I would have been greater than they all!”
Hart makes a compelling case that fame is not synonymous with trust, respect, or value of contribution. Hart’s emphasis on knowing one’s principles and holding fast to them, caused great introspection. I walked away from the book desiring to be a better strategist — to think and plan further ahead in my own life and endeavors.
